“DDoS” is the acronym for distributed denial-of-service. A distributed denial-of-service attack means an attempt to disrupt the normal traffic in a particular/targeted server by making a huge number of requests from various computers and causing massive traffic in that targeted server to cause service interruption.
These attacks achieve success by destroying service to normal users through directing huge traffic from compromised multiple computers or different network devices such as IoT devices.

For example, when you are going for a trip on vacation, and suddenly you stop at a point due to a huge traffic jam consisting of cars lined up for miles on that road, you check your GPS, and there’s no way out!
So, standing cars are the flooded requests made by the attacker, and you are the normal user unable to use the service (here, in a sense, the road).
So that explains what is a DDoS attack. Now let’s see how this kind of attack works.
Table of Contents

DDoS attacks are mainly carried out by compromised devices consisting of computers, mobile phones, network devices, IoT devices etc. These compromised devices are called bots, and a network comprising of these bots, called a botnet, is single-handedly operated by an attacker to perform a DDoS attack on targeted servers.
Here’s how a botnet can be created.
At first, an attacker (hacker) targets hundreds or thousands of devices to infect those devices with malicious software, aka virus.
To create/build a Botnet, an attacker (hacker) injects malicious software that propagates and gradually takes over more and more computers, or that attacker might find an IoT device with vulnerability and build a bot to scan the internet and hack as many devices as possible.
This is how an attacker/hacker creates a Botnet.
Devices under the attacker’s control obey the command the attacker sends to execute through them. Simply put, the attacker controls all devices simultaneously to make a DDoS attack. The hacker can issue a command, and all the devices do whatever the hacker wants to do.
The attacker will execute the attack whenever they want after establishing the Botnet. They just flood the targeted server with a huge number of requests.
There are some common types of DDoS attacks:
| Application Layer Attacks | This DDoS attack drains the resources of the targeted server to create a denial-of-service. |
| Protocol Layer Attacks | This DDoS attack aims to exhaust the state of the targeted server to cause a service disruption by over-consuming server resources like firewalls and load balancers. |
| Volumetric Layer Attacks | This DDoS attack aims to create congestion between the target and the internet by consuming all available bandwidth. |
Now, let’s see how these attacks take place.
The goal of this attack is to drain the resources of the targeted server to create a denial-of-service. As the name refers to the Application layer (layer 7 in the OSI model), this attack is targeted at the server where web pages are created and delivered in response to HTTP requests.
This attack is similar to refreshing the web page in a web browser over and over on many devices simultaneously. These large numbers of HTTP requests flood the targeted server, and it results in denial-of-service. This attack is called “HTTP flood”. It may be simple or complex. If it’s simple, it may access one URL with the same range of attacking IP addresses; if it’s complex, it may use many IP addresses and target random URLs using random user agents.

This attack aims to exhaust the state of the targeted server to cause a service disruption by over-consuming server resources like firewalls and load balancers. This attack focuses on layer 3 and layer 4 in the OSI model to render the target inaccessible.

This attack exploits TCP Handshake – the sequence of communications by which two computers initiate a network connection. The attacker exploits by sending many TCP (Initial Connection Request) and SYN packets with spoofed source IP addresses. Then, the target machine responds to every request and waits for the final step in the handshake, which never occurs, ultimately exhausting the target’s resources.
This attack aims to create congestion between the target and the Internet by consuming all available bandwidth. In this attack, large amounts of data are sent to the target or any form of amplification is attacked by a botnet.

DNS amplification is an example of Volumetric attacks. By requesting an open DNS server with a spoofed IP address (the IP address of the victim), the target IP address receives a response from the server. With very little effort, a long response is generated.
These are some of the common DDoS attacks.
Distributed denial of service attacks usually involves taking advantage of huge traffic on a server to either disrupt a broadcast of information or to stop particular users from taking advantage of that server. The motives behind what is a ddos attack are not always clear, and that is why experts have tried to understand patterns and the kind of data blocked to point out some common reasons behind DDoS attacks. DDoS attacks are carried out by individuals, teams, or even countries with their own purposes. Some of the common reasons why a distributed denial of service attack is carried out are:
Vandalism in the world of the internet is most often nothing but frustrated young adults wanting to either impress their peers or to take out their anger. Cyber vandalism usually occurs on a smaller scale and the attacks last for a very little time. Sometimes, the attackers even use hired DDoS attackers to carry out their frustrations.
One of the most common reasons behind DDoS attacks are extortion of money, services or information from the receiving end. MeetUp, Bitly, Vimeo, etc. are some companies that have been victims of such attacks. Usually, the party wanting to extort something carries out the DDoS attack indirectly through hired ‘stressers’ and ‘boosters’ (fancy names for DDoS attackers).
Now entering the serious domain, DDoS attacks also have business reasoning behind them. A lot of attacks have been carried out to stop users from taking part in a major event from a business. Such cyber attacks are usually well funded and the cost can go up to $40,000 per hour. It can also be performed to shut down online businesses.
One war can be fought on the land with soldiers, another one can be fought using tech savvy professionals and a server block. Nations have carried out DDoS attacks against their own critics and also on other countries. Usually, these attacks are carried out to disrupt wealth flow, infrastructure progress or spread of a particular kind of information.
Often DDoS attacks are used in such cases where a person wants to carry out revenge or compete unethically. It usually involves disrupting the servers of an online game or taking advantage of the game server to gain an edge. Sometimes even stressers and boosters are hired by rivals to disrupt a service for a long time or even permanently.
DoS stands for a denial of service attack, as opposed to a DDoS or a distributed denial of service) attack. There are several significant differences between the two, namely:
A general DDoS attack would manipulate many distributed network devices between the attacker and the victim into making an attack, thus exploiting what is otherwise legitimate behavior. However, a traditional DoS attack doesn’t use multiple distributed devices and does not even focus on devices between the attacker and the organization. What’s more, a typical DoS attack does not usually employ multiple internet devices either.
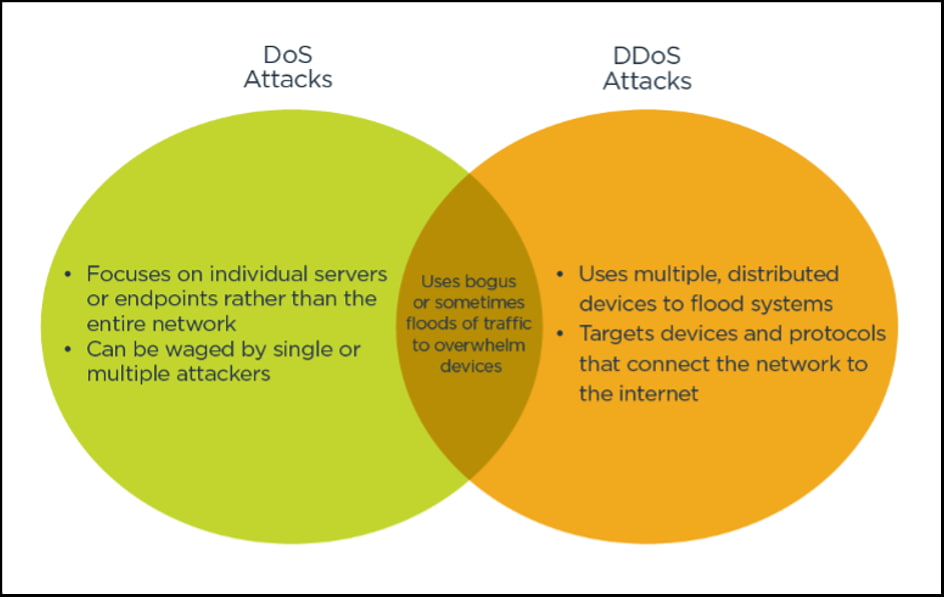
Some typical DoS attacks can include ones like:
These aforementioned DoS attacks can all be resolved by fixing the host or filtering out the traffic. Therefore, they are vastly different from DDoS attacks, where the bad actor begins with a resource consumption strategy so they can use legitimate requests to overwhelm systems.
The first sign of a DDOS attack is that the website becomes slow or unavailable suddenly. So how can you identify what is a DDoS attack being made on a network? Some other technical signs that you can look for may include:
This is how an attacker or hacker performs a DDoS attack. A DDoS attack is an illegal and punishable act by law. Having an appropriate level of knowledge about the standards and best practices concerning IT security can help any team or organization to respond to DDOS attacks.
The primary concern when it comes to mitigating a DDoS attack is to separately identify attack traffic and normal traffic. While cutting off all traffic on a website would be a mistake, if a website suddenly sees a surge in traffic from known cyber attackers, mitigating a possible DDoS attack is necessary.
However, the difficult part is, once again, telling legitimate users apart from attackers. The more complex a DDoS attack, the more difficult it is to separate it from normal traffic since an attacker would try to blend in with the normal traffic as much as they can.
Here are some methods for DDoS mitigation:
A very basic precaution to prevent this kind of attack would be for organizations to regularly conduct risk assessments and audits on all their devices, servers, and overall network. It’s true that regular risk assessment can not guarantee the complete avoidance of DDoS attacks, but knowing the vulnerabilities of an organization’s network can still help you understand which strategies can lessen the effects of a DDoS attack.
Another way to thwart a DDoS attack would be to create another route called a ‘blackhole route’ and funnel traffic into that one. Once you implement blackhole filtering without any specific criteria for restriction, both the legitimate and malicious network traffic is sent to a null route that is the black hole and simultaneously dropped from the network.
However, once a website experiences a DDoS attack, rerouting all network traffic into a blackhole as a defense actually gives the attacker(s) their desired goal by rendering the network inaccessible. Therefore, the blackhole routing is not an ideal solution for DDoS mitigation by any means.
Once you suspect a DDoS attack aimed at you, a very good way to make sure you don’t shut down network traffic altogether (eliminating the normal traffic along with the bad one in the process) would be to determine the source and the quality of the suspicious traffic. One way to do this would be to use an Anycast network to scatter the attack traffic throughout a network of distributed servers as a solid DDoS mitigation strategy. This is done so that all of the traffic is absorbed by the network and made more manageable.
Limiting the number of requests a server can accept over a specific time window is also a good way to mitigate distributed denial-of-service attacks. However, it’s to be noted that while rate limiting can be useful in slowing web scrapers from stealing any content and also for mitigating brute force attempts at login, it can’t handle a more complex DDoS attack all on its own.
Still, rate limiting can definitely be a useful component while planning a DDoS mitigation strategy.
Web Application Firewalls or WAFs, generally used to filter out and monitor HTTP traffic, can also be used to mitigate distributed denial-of-service attacks. A WAF is an appliance that stands between the internet and a company’s servers and plays the role of a reverse proxy. With firewalls, an organization gets to create a set of rules according to their preferences that filter out requests. You can start with a basic set of rules and go on to modify them on the basis of what you observe regarding patterns of suspicious or malicious activities that might be related to a DDoS attack.
WAF is also best used in harmony with some other services and devices when it comes to building a defense mechanism for DDoS mitigation.
As mentioned before, an Anycast network can be used for traffic differentiation. An Anycast network would help with scattering the attack traffic throughout a network of distributed servers, so that the traffic is then absorbed by the network. The help of an Anycast network is indeed excellent when it comes to forming a sturdy mitigation strategy for types of DDoS attacks, and having an easier time managing a network.
In the past, there have been several DDoS attacks that have disrupted data from several big platforms. Some of the examples of such attacks are:

Distributed denial-of-service attacks vary based on length and sophistication. So a DDoS attack can happen over a long period of time, or it can be very short in length. When a DDoS attack lasts over several hours or even days, it is obviously considered a long-term attack. However, there are also burst attacks that are waged over a very short period of time: a few minutes or even mere seconds. Burst attacks are naturally more difficult to trace since they don’t go on for long.
A fully-equipped DDoS solution would include components that can aid an organization in both defense and monitoring. Keep in mind that a good DDoS protection solution would employ a whole range of tools that can provide safety against every type of distributed denial-of-service attack and monitor thousands of parameters at once.
A distributed denial of service attack is a cyber attack in which infected computers act as hosts for the attackers to invade a server in large numbers, causing a service disruption. The attack can be performed against network resources and websites with various motives.
In order for a DDoS attack to work, the attackers have to create a command and control server that is called a botnet. It consists of several infected computers, called zombies or bots. There is no upper limit to the number of bots in a botnet and the attack can be carried out easily by just directing the botnet to a server.
One of the biggest DDoS attacks was carried out against GitHub in 2018 when its complete operations were stopped by the attackers. The attack lasted for 20 minutes and reached 1.3 Tbps, sending the packets at a rate of 126.9M per second. The attackers magnified the attack by 50,000 times against the affected server.
Layer 1 Crypto Projects 2022 | What is Miner Extractable Value | What is Decentralization | How to Make and Sell NFT | Best Blockchain Bridge | Advantages and Disadvantages of Blockchain Technology | Layer 1 Blockchain Protocols | Blockchain Features and Benefits | How Altcoins Work | How Proof of Work Works | Crypto Cloud Mining | What is Proof of Stake in Blockchain | What is Fiat Currency | Types of Nodes in Blockchain | What is Nonce in Blockchain | What is DLT in Blockchain | What is Ethereum Merge | What is Physical Layer in OSI Model | What is a Blockchain Fork
Author Bio
Sams is a tech student who explores web3 enthusiastically. (Twitter: @vamsikrishnaut1)